Η Check Point Research (CPR) has detected six applications in Play Store of Google that spread malware by pretending to be antivirus solutions.
Γknown as Sharkbot, malware steals credentials and banking information. During her research, the CPR counted over 1.000 unique IPs addresses of infected devices, mainly in the United Kingdom and Italy. However, his statistics Google Play Store revealed that the malicious applications were downloaded more than 11.000 times.

The Sharkbot lures its victims through alerts push and tricking users into entering credentials into environments that mimic data entry forms. THE CPR suspects the threat is Russian-speaking and warns Android users around the world to be extra careful before downloading antivirus solutions on Play Store.

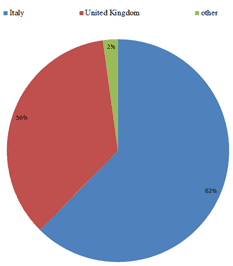
- The 62% of the victims was found in Italy, 36% in the UK, 2% in other countries
- Threat operators have implemented geographical fencing, which ignores device users in China, India, Romania, Russia, Ukraine and Belarus
- CPR immediately reported the her findings on Google, which removed the malicious applications
Η Check Point Research (CPR) He discovered six applications which spread banking malware on the Google Play Store as disguised as antivirus solutions. Malware, known as "SharkbotSteals credentials and banking information of Android users. The Sharkbot entices its victims to insert their credentials into windows that mimic credential entry forms. When a user enters their data there, the compromised data is sent to a malicious server. THE CPR found that malware creators had implemented a geolocation feature that ignores device users in the China, India, Romania, Russia, Ukraine or Belarus.
The Six Malicious Applications

Four of the applications came from their three developer accounts Remainder Adamcik, Adelmio Pagnotto and Bingo Like Inc. When CPR checked the history of these accounts, they found that two of them were active in the fall of 2021. Some of the apps linked to these accounts were removed from Google Play, but still exist in informal markets. This could mean that the person behind the applications is trying to stay "under the radar" while still engaging in malicious activity.
The Victims
CPR was able to collect statistics for a week. During this period, he counted more than 1.000 IP victims. Every day, the number of victims was increasing by about 100. According to his statistics Google Play, the six malicious applications detected by CPR were downloaded more than 11.000 times. Most of the victims are in the United Kingdom and Italy.
Figure 2.% of victims per country
The Methodology of Attack
- Motivate the user to grant access rights to an application
- After that, the malware gains control of a large part of the victim's device
- Threat-takers can also send push alerts to victims that contain malicious links
Details of the attack
CPR does not have enough data to attribute the responsibility to a specific location. We can assume that the malware authors speak Russian. In addition, the malware will not perform its malicious functionality if the device is locally located in China, India, Romania, Russia, Ukraine or Belarus.
We announce responsibly
Immediately after locating these applications that spread Sharkbot, CPR announced its findings to Google. After reviewing the applications, Google proceeded to permanently remove these applications from the Google Play store. The same day that CPR reported the findings to Google, the NCC team he published a separate research for Sharkbot, citing one of the malicious applications.
His comment Alexander Chailytko, Cyber Security, Research & Innovation Manager, Check Point Software:
I think it's important for all Android users to know that they need to be very careful before downloading any antivirus solution from the Play Store. It could be Sharkbot.
Security Tips for Android Users
- Only install applications from trusted and verified publishers.
- If you see an application from a new publisher, look for one from a trusted one.
- Report to Google any seemingly suspicious applications you encounter.
 Do not forget to follow it Xiaomi-miui.gr on Google News to be informed immediately about all our new articles! You can also if you use RSS reader, add our page to your list by simply following this link >> https://news.xiaomi-miui.gr/feed/gn
Do not forget to follow it Xiaomi-miui.gr on Google News to be informed immediately about all our new articles! You can also if you use RSS reader, add our page to your list by simply following this link >> https://news.xiaomi-miui.gr/feed/gn
Follow us on Telegram so that you are the first to learn our every news!