Η Check Point Research, the Threat Intelligence its research department Check Point Software Technologies Ltd., the world's leading provider of cyber security solutions, published the Global Threat Index for December 2021.
Σe a month we saw the vulnerability apachelog4j to scan the internet, the researchers reported that Trickbot is still the most common malware, albeit at a slightly lower rate, 4%, impact of organizations worldwide, by 5% In November.

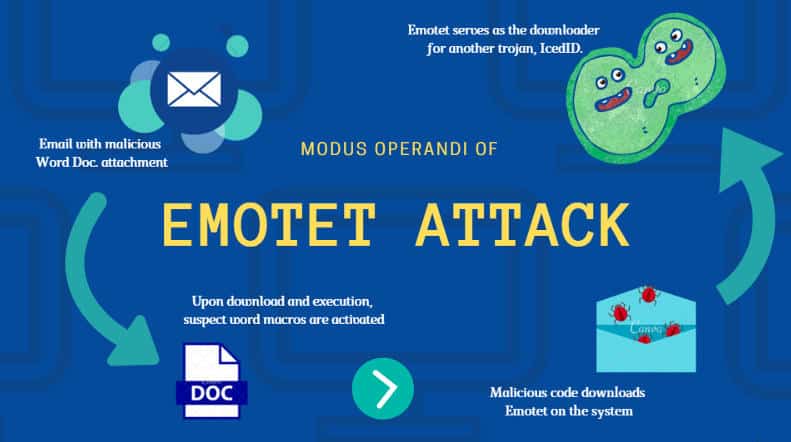
Recently it also recovered Emotet, which quickly climbed from seventh to second place. THE CPR also reveals that the industry that receives the most attacks is still Education / Research.
In December, the “Apache Log4j Remote Code ExecutionIs the vulnerability with the highest frequency of exploitation, affecting it 48,3% of organizations worldwide. The vulnerability was first reported on December 9 in its recording package apachelog4j - the most popular Java log library used in many Internet services and applications with over 400.000 downloads from the GitHub Project.

The vulnerability has created a new scourge, affecting almost half of the world's companies in a very short time. Attackers are able to take advantage of vulnerable applications to execute cryptojackers and other malicious software on compromised servers. Until now, most attacks have focused on the use of cryptocurrencies to the detriment of victims, however, the more sophisticated perpetrators have begun to act aggressively and exploit the breach for high-value targets.
The same month we also saw the Emotet botnet move from seventh to second most common malware. Just as we suspected, Emotet did not take long to lay a solid foundation since its reappearance last November. It is misleading and spreads quickly through phishing emails with malicious attachments or links.
It is now more important than ever for everyone to have a strong email security solution and to ensure that users know how to identify a suspicious message or attachment. said Maya Horowitz, vice president of research at Check Point Software.
Η CPR states that in the month of December the Education / Research is the most attacked industry in the world, followed by the Government / Armed Forces and the ISP / MSP. Vulnerability "Apache Log4j Remote Code ExecutionIs the most frequently exploited, affecting it 48,3% organizations worldwide, followed by the "Web Server Exposed Git Repository Information Disclosure”Which affects the 43,8% of organizations worldwide. THE "HTTP Headers Remote Code ExecutionRemains third on the list of most frequently exploited vulnerabilities, with a global impact 41,5%.

Top malware groups
* The arrows refer to the change of the ranking in relation to the previous month.
This month, Trickbot is the most prevalent malware affecting 4% of organizations worldwide, followed by Emotet and Formbook, both with a global impact of 3%.
1. ↔ Trickbot - Trickbot is a modular Botnet and Banking Trojan which is constantly updated with new features, characteristics and distribution channels. This allows Trickbot be a flexible and customizable malware that can be distributed as part of multi-purpose campaigns.
2. ↑ Emotet Emotet is an advanced, self-replicating and modular Trojan. Emotet was once used as a banking Trojan, but has recently been used as a distributor for other malware or malware campaigns. Uses multiple methods to maintain obsession and avoidance techniques to avoid detection. Additionally, it can spread through spam phishing messages that contain malicious attachments or links.
3. ↔ Formbook - Formbook is an InfoStealer that collects credentials from various web browsers, collects screenshots, monitors and records keystrokes, and can download and execute files according to C&C commands.
Leading attacks in industries worldwide:

This month, Education / Research is the industry with the most attacks worldwide, followed by the Government / Armed Forces and the ISP / MSP.
1. Education / Research
2. Government / Armed Forces
3. ISP / MSP
The top exploiting vulnerabilities
In December, the “Remote execution of Apache Log4j codeIs the most commonly exploited vulnerability, affecting it 48,3% organizations worldwide, followed by the "Disclosure of information Git Repository Web Server Exposed”Which affects the 43,8% of organizations worldwide. THE "HTTP Headers Remote Code ExecutionRemains third on the list of most frequently exploited vulnerabilities, with a global impact 41,5%.
1. Ap Remote execution of Apache Log4j code (CVE-2021-44228) There is a remote code execution vulnerability in apachelog4j. Successfully exploiting this vulnerability could allow a remote intruder to execute arbitrary code on the affected system.
2. ↔ Web Server Exposed Git Repository Information Disclosure - A vulnerability was reported in the Git Repository. Successfully exploiting this vulnerability could allow unintentional disclosure of account information.
3. ↔ HTTP Headers Remote Code Execution (CVE-2020-10826, CVE-2020-10827, CVE-2020-10828, CVE-2020-13756) HTTP headers allow the user and the server to forward additional information with an HTTP request. A remote intruder can use a vulnerable HTTP header to execute arbitrary code on the victim's machine.
Top Malicious Mobile Apps

The AlienBot ranks first in the most prevalent malware for mobile, followed by xHelper and FluBot.
1. AlienBot - The malware family AlienBot it is a Malware-as-a-Service (MaaS) for Android devices that allows a remote intruder, as a first step, to enter malicious code into legitimate financial applications. The attacker gains access to the victims' accounts and eventually takes full control of their device.
2. xHelper - A malicious application that has been in the forefront since March 2019 and is used to download other malicious applications and display ads. The application is capable of being hidden from the user and can even be reinstalled if it has been uninstalled.
3. FluBot - The flubot it is a Android botnet which is distributed via SMS phishing messages, which are most often pretended to be delivery companies. As soon as the user clicks on the link in the message, FluBot is installed and accesses all the sensitive information on the phone.
The complete list of the most common malware threats in Greece for December 2021 is:
Formbook - FormBook was first identified in 2016 and is an InfoStealer targeting the Windows operating system. It is marketed as MaaS in underground hacking forums for its powerful avoidance techniques and relatively low price. FormBook collects credentials from various web browsers, collects screenshots, monitors and records keystrokes, and can download and execute files as instructed by its C&C.
Emotet- Emotet is an advanced, self-replicating and modular Trojan that was once used as a banking Trojan and now distributes other malicious programs or malicious campaigns. Emotet uses multiple methods to maintain its obsession and avoidance techniques to prevent detection and can be spread through spam emails that contain malicious attachments or links.
AgentTesla - AgentTesla is an advanced RAT (Trojan Remote Access) that acts as a keylogger and password thief. Active since 2014, AgentTesla can track and collect victim input's keyboard and clipboard, and capture screenshots and extract credentials for a variety of software installed on the victim's machine (including Chrome, Mozilla Firefox and Microsoft Outlook email client). AgentTesla sells openly as a legal RAT with customers paying $ 15- $ 69 for licenses.
Trickbot - Trickbot is a modular Botnet and Banking Trojan that targets the Windows platform and is distributed primarily through spam campaigns or other malware families such as Emotet. Trickbot sends information about the infected system and can also download and execute arbitrary modules from a wide range of available modules: from a VNC module for remote control to an SMB module for distribution within a compromised network. Once a machine is infected, the Trickbot gang, the menacing agents behind this malware, use this wide range of modules not only to steal bank credentials from the target computer, but also to move around and identify itself. target organization, before launching a targeted ransomware attack across the company.
Joker - An android Spyware on Google Play, designed to steal SMS messages, contact lists and device information. In addition, the malware silently signals to the victim for premium services on advertising sites.
Dridex- Dridex is a Windows Trojan-targeted banking Trojan that is observed to be distributed through spam campaigns and Exploit Kits, which relies on WebInjects to spy on and redirect bank credentials to a server controlled by an attacker. Dridex communicates with a remote server, sends information about the infected system, and can also download and run additional drives for remote control.
Vidar - Vidar is an infolstealer targeting Windows operating systems. It was first detected in late 2018 and is designed to steal passwords, credit card data and other sensitive information from various internet browsers and digital wallets. Vidar has been sold on various online forums and is used as a malware dropper that downloads ransomware GandCrab as a secondary payload.
Cryptbot - Cryptbot is a Trojan that infects systems by installing a rogue VPN program and steals stored browser credentials.
Teabot - Teabot malware is an Android Trojan threat used in phishing attacks. Once Teabot is installed on the compromised device, it can stream the screen live to the perpetrator, as well as use the Accessibility Services to perform other malicious activities.
Triada - Triada is a modular backdoor for Android, which provides super-user privileges for downloading malware. Triada has also been observed to tamper with URLs loaded in the browser.
XMRig - XMRig, first introduced in May 2017, is an open source CPU mining software used to extract Monero cryptocurrency.
The top 10 in Greece |
|||
| Malware name | Global Impact | Impact on Greece | |
| Formbook | 3.17% | 17.58% | |
| agent Tesla | 2.10% | 4.61% | |
| Trickbot | 4.30% | 3.17% | |
| Joker | 0.08% | 2.02% | |
| Dridex | 1.74% | 2.02% | |
| Vidar | 0.91% | 2.02% | |
| Cryptobot | 0.50% | 1.73% | |
| Ramnit | 1.74% | 1.73% | |
| Teabot | 0.07% | 1.73% | |
| Triada | 0.13% | 1.73% | |
The World Threat Impact List and the Map ThreatCloud by Check Point Software, based on ThreatCloud intelligence of the Company, in the largest cooperation network for the fight against cybercrime, which provides data on the threats and trends prevailing in attacks, utilizing a global network of threat detectors.
The database ThreatCloud includes over 3 billion websites and 600 million files daily and locates more than 250 million malware activities every day.
 Do not forget to follow it Xiaomi-miui.gr on Google News to be informed immediately about all our new articles! You can also if you use RSS reader, add our page to your list by simply following this link >> https://news.xiaomi-miui.gr/feed/gn
Do not forget to follow it Xiaomi-miui.gr on Google News to be informed immediately about all our new articles! You can also if you use RSS reader, add our page to your list by simply following this link >> https://news.xiaomi-miui.gr/feed/gn
Follow us on Telegram so that you are the first to learn our every news!