The team of Chippers which is behind its distribution Roaming Mantis malware, updated the Android version of the malware to include a DNS converter
His method DNS changer modifies DNS settings on vulnerable WiFi routers to spread the infection to other devices.

By September 2022, security researchers noticed that the group of hackers behind the malware of “Roaming Mantis”, they proceeded to distribute a new version of the malware Wroba.o/XLoader on Android, which detects vulnerable WiFi routers based on their model, and changes their DNS.
The malware then creates a request HTTP to tamper with the DNS settings of a vulnerable WiFi router, causing connected devices to be redirected to malicious websites that host phishing forms or drop Android malware.
The new variant of the malware Wroba.o/XLoader for Android discovered by them Kaspersky researchers, The who have been monitoring Mantis' broadcast activity for years. Kaspersky explains that the Roaming Mantis uses his method DNS hijacking at least since 2018, but the new element in its recent release is that the malware targets specific routers.
The latest campaign using this updated malware targets specific models of WiFi routers that are mainly used in South Korea. However, hackers can change it at any time to include other routers commonly used in other countries.
This approach allows them to perform more targeted attacks and compromise only specific users and areas, avoiding detection in all other cases.
Previous Roaming Mantis attacks targeted users from Japan, Austria, France, Germany, Turkey, Malaysia and India.
A new router DNS resolver
Its latest editions Roaming Mantis use SMS phishing texts (smishing) to direct targets to a malicious website.
If the user's device is Android, it will ask the user to install one malicious APK, which is loaded with the malware Wroba.o/XLoader, while contrary to users Apple iOS, the landing page will redirect users to a phishing page that attempts to steal credentials.

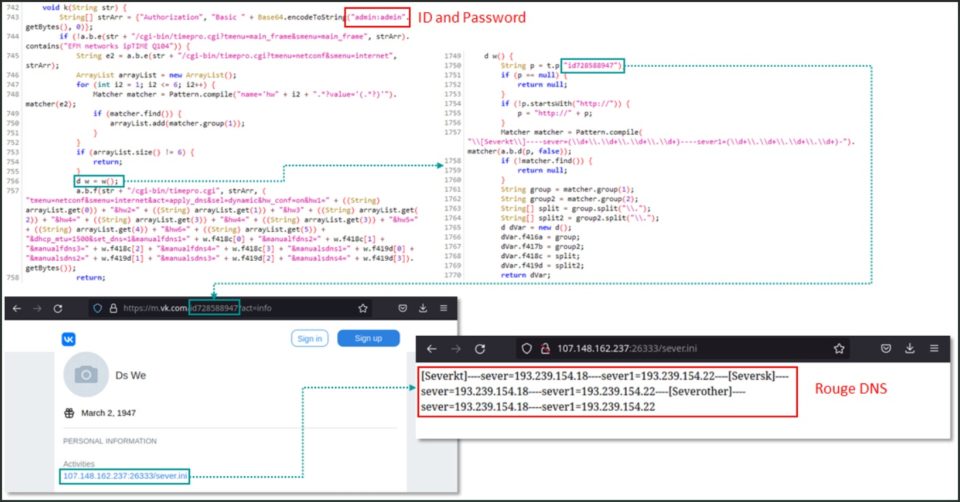
Once the XLoader malware is installed on the victim's Android device, it obtains the default gateway IP address from the connected WiFi router, and then tries to access the router's admin menu using a default password to discover the device model .
XLoader now features 113 hardcoded strings with code used to probe into specific models of WiFi routers – and if a match is found, the malware proceeds to hack DNS by changing the router's settings.
Η Kaspersky states that DNS changer uses default credentials (admin / admin) to access the router, and then make changes to the DNS settings using different methods depending on the model detected.
Analysts also explain that the DNS server used by the Roaming Mantis, only changes certain domain names to certain landing pages when accessed from a Smartphone.
The spread of infection

With the DNS settings on the router now changed, when other Android devices connect to the WiFi network, they will automatically be redirected to the malicious landing page and prompted to install the malware.
This fact creates a constant flow of infected devices to further hack other clean WiFi routers in public networks, serving a large number of people in the country.
Η Kaspersky warns that this feature gives the Roaming Mantis team the ability to expand dangerously, allowing malware to spread unchecked.
Even though there are no landing pages located on USA and Roaming Mantis does not appear to actively target router models in use in the country, its statistics Kaspersky they show that 10% of all XLoader victims are in the US.
Users can protect themselves from its attacks Roaming Mantis avoiding clicking on links received via SMS, however, is even more important avoid installing an APK outside of the Google Play Store.
 Do not forget to follow it Xiaomi-miui.gr on Google News to be informed immediately about all our new articles! You can also if you use RSS reader, add our page to your list by simply following this link >> https://news.xiaomi-miui.gr/feed/gn
Do not forget to follow it Xiaomi-miui.gr on Google News to be informed immediately about all our new articles! You can also if you use RSS reader, add our page to your list by simply following this link >> https://news.xiaomi-miui.gr/feed/gn
Follow us on Telegram so that you are the first to learn our every news!